Overview
AWS STS (Security Token Service) Integration allows the Dataloop platform to securely assume AWS roles and obtain temporary security credentials for accessing AWS resources. This integration enhances security by providing time-limited access to AWS services and resources without the need to manage long-term access keys.
We recommend selecting Cross-Account as the integration type. It is AWS’s most secure option and provides enhanced protection for your data.
Only users with the Organization Admin or Owner roles are authorized to create integrations. Learn more
To set up STS in AWS and connect it to Dataloop, the following process involves:

1. Create an S3 Bucket
- Log in to the AWS Management Console.
- Go to Services > Storage and click the S3 service.
- Click Create bucket. The Create Bucket page is displayed.
- Provide a Bucket name.
- Select your AWS region from the list.
- Ensure you block public access settings for this bucket - Block all public access.
- For all other optional settings, use the default values.
- Click Create bucket. A confirmation message is displayed.
For a step-by-step guide on creating an S3 bucket in AWS, see Creating a bucket.
2. Create an IAM Policy
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Select the IAM service from the list.
- Click on Policies from the left navigation panel.
- Click Create policy. The Create Policy page is displayed.
- Select the JSON tab and define the policy document in the following JSON format:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowListBucket",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:PutObject",
"s3:DeleteObject",
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::<DataloopBucketName>",
"arn:aws:s3:::<DataloopBucketName>/*"
]
}
]
}
Replace <DataloopBucketName> with the name of the your S3 bucket.
- Click Next.
- Enter a Name for the policy and an optional Description.
- Click Create policy. A confirmation message is displayed.
s3:DeleteObjectaction allows Dataloop platform to delete dataset items, see downstream.- The resource
arn:aws:s3:::<DataloopBucketName>is required for theListBucketaction.
For a step-by-step guide on creating an IAM policy in AWS, see Creating IAM policies.
3. Create an IAM User
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Click the IAM service from the list.
- From the left portal menu, click Users.
- Click Add users.
- Enter a username.
- Ensure the Programmatic access checkbox is selected as the type of access you want to grant the user.
Note: Use the default access type and do not choose console access. - Click Next. A Set Permissions page is displayed.
- Leave the page as is and click next.
- Click Create user. A confirmation message is displayed.
See Creating an IAM user in AWS for more information.
4. Create an IAM Role
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Click the IAM service from the list.
- From the left portal menu, click Roles.
- Click Create role.
- Choose AWS service as the trusted entity type.
- Choose EC2 as the use case.
- Click Next.
- Search and select the policy that you created for accessing the S3 bucket.
- Click Next.
- Enter a name and an optional description for the role.
- Click Create role. A confirmation message is displayed.
- Click the Role that you created from the list.
- Copy the ARN value, which is required during the integration phase.
- For a step-by-step guide on creating an S3 bucket in AWS, see Creating IAM roles.
5. Add an Inline IAM Policy to the IAM User
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Click the IAM service from the list.
- From the left portal menu, click Users.
- Search and select the IAM user you just created.
- Click on the Permissions tab
- Click on the Add permissions button and choose Create inline policy
- Select the JSON tab
- Define policy document in JSON format, like:
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<YourAWSAccountId>:role/<IAMRoleName>"
}
}
- Replace
<YourAWSAccountId>with your AWS account ID. - Replace
<IAMRoleName>with the name of the IAM Role.
- Click Review Policy.
- Enter a Name for the policy.
- Click Create policy. A confirmation message is displayed.
6. Create an Access Key for the IAM User
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Click the IAM service from the list.
- From the left portal menu, click Users.
- Find and click on the desired user (for example, a Dataloop user) for whom you want to create an access key.
- Click on the Security credentials tab.
- In the Access keys section, click Create access key.
- In the Access key best practices & alternatives, choose Application running outside AWS.
- Click Next.
- Enter a description that includes Dataloop.
- Click Create access key.
- Copy and save the Access Key and Secret Access Key in a secure location, or download the CSV file. The access key and secret access key are required for the integration phase.
- Click Done. It completes the access key creation process for the IAM user.
7. Update the Trust Relationship of the IAM Role
- Log in to the AWS Management Console.
- Go to Services and click All services. A list of services is displayed.
- Click the IAM service from the list.
- From the left portal menu, click Roles.
- Search and select the IAM role whose trust relationship you want to change.
- Click the Trust relationships tab.
- Click Edit trust policy.
- Replace the existing trust policy JSON document with the following:
{ "Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS":"arn:aws:iam::<AWSAccountId>:user/<IAMUserName>"
},
"Action": "sts:AssumeRole"
}
]
}
- Replace
<AWSAccountId>with your AWS account ID. - Replace
<IAMUserName>with the name of the IAM User.
- Click Update Policy. A confirmation message is displayed.
8. Create the AWS STS Integration
Only users with the Organization Admin or Owner roles are authorized to create integrations. Learn more
- Log in to the Dataloop platform.
- From the left-side panel, select Integrations.
- Click Create Integration -> Create Storage Integration. A pop-up window is displayed on the right-side.
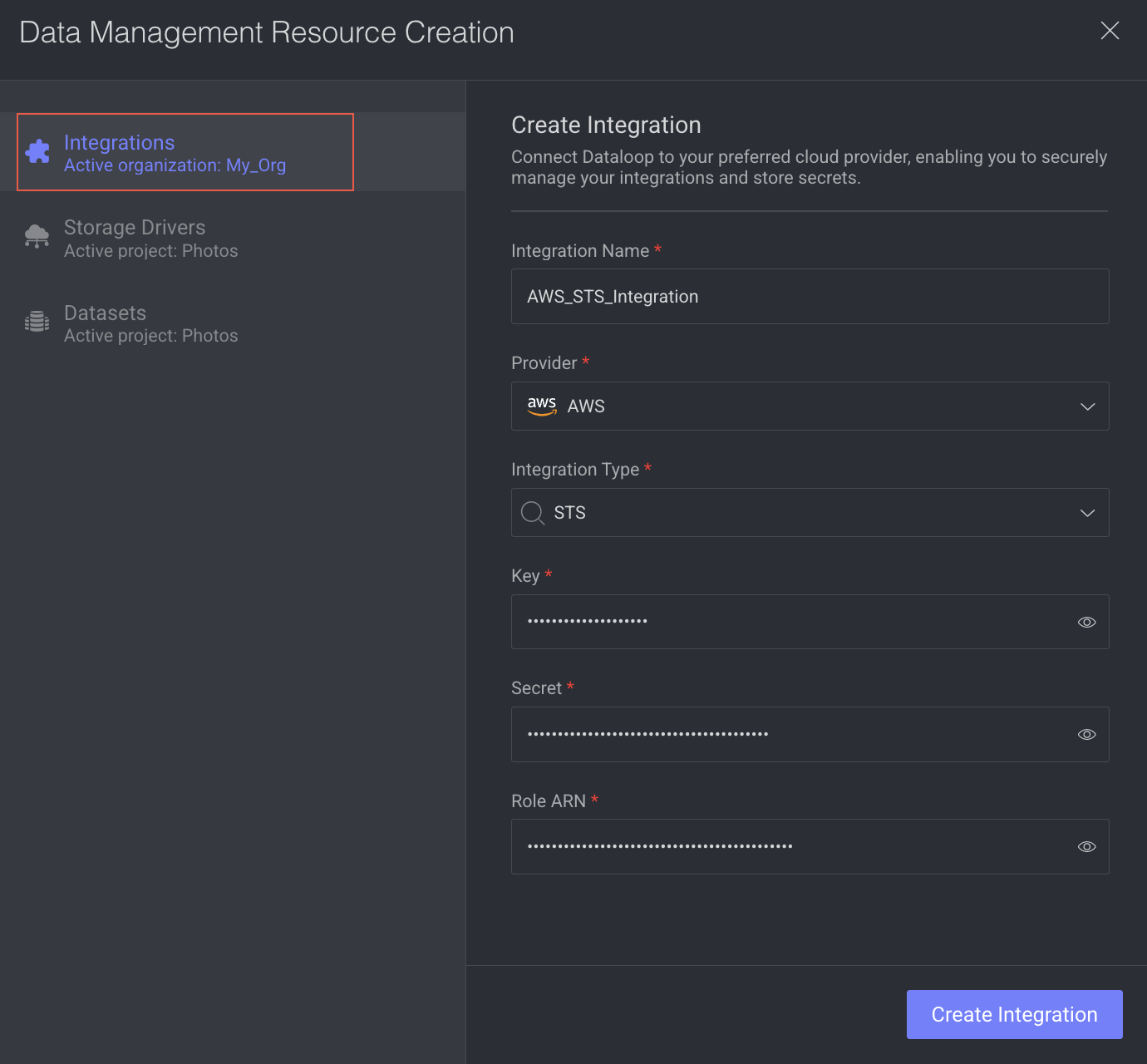
- Integration Name: Enter a Name for the integration.
- Provider: Choose AWS from the list.
- Integration Type: Select the STS from the list.
- Key: Enter the IAM user’s access key ID that you noted while creating an access key for the IAM user.
- Secret: Enter the IAM user’s secret access key that you noted while creating an access key for the IAM user.
- Role ARN: Enter the Role ARN that you noted earlier.
- Click Create Integration. A confirmation message is displayed.
9. Create S3 Storage Driver
For more information, see the Create AWS S3 Storage Driver topic.